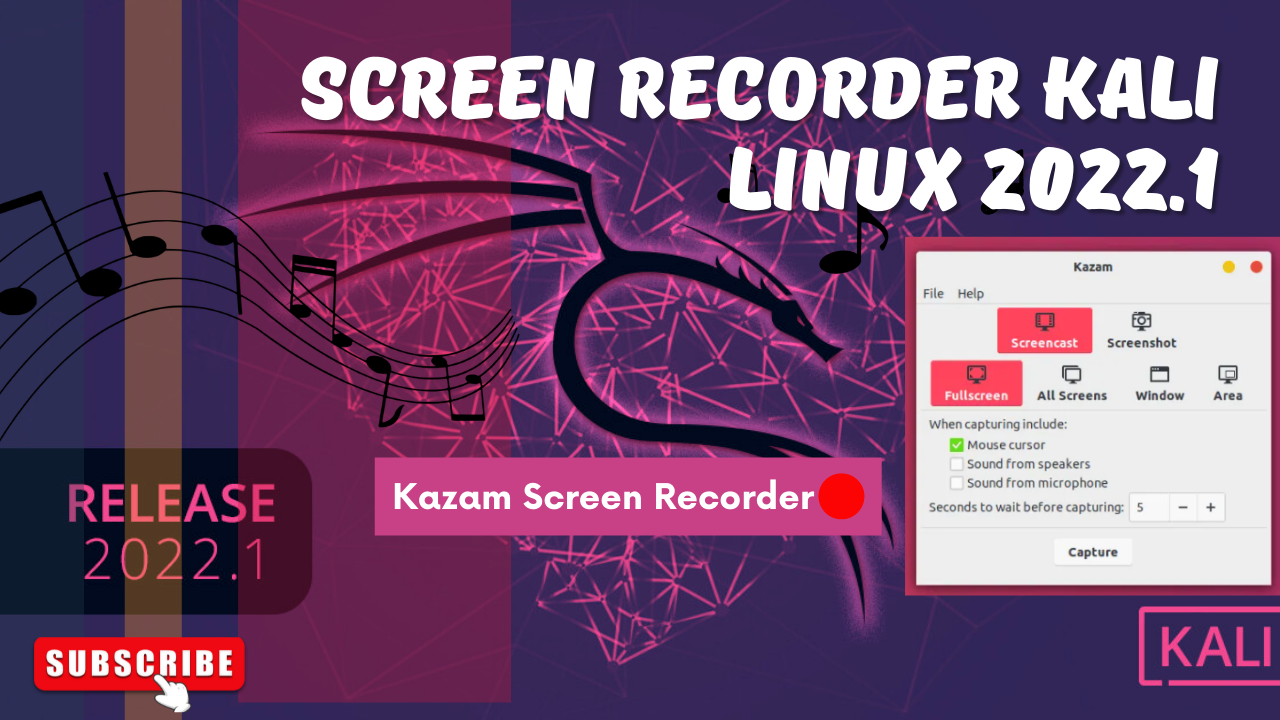
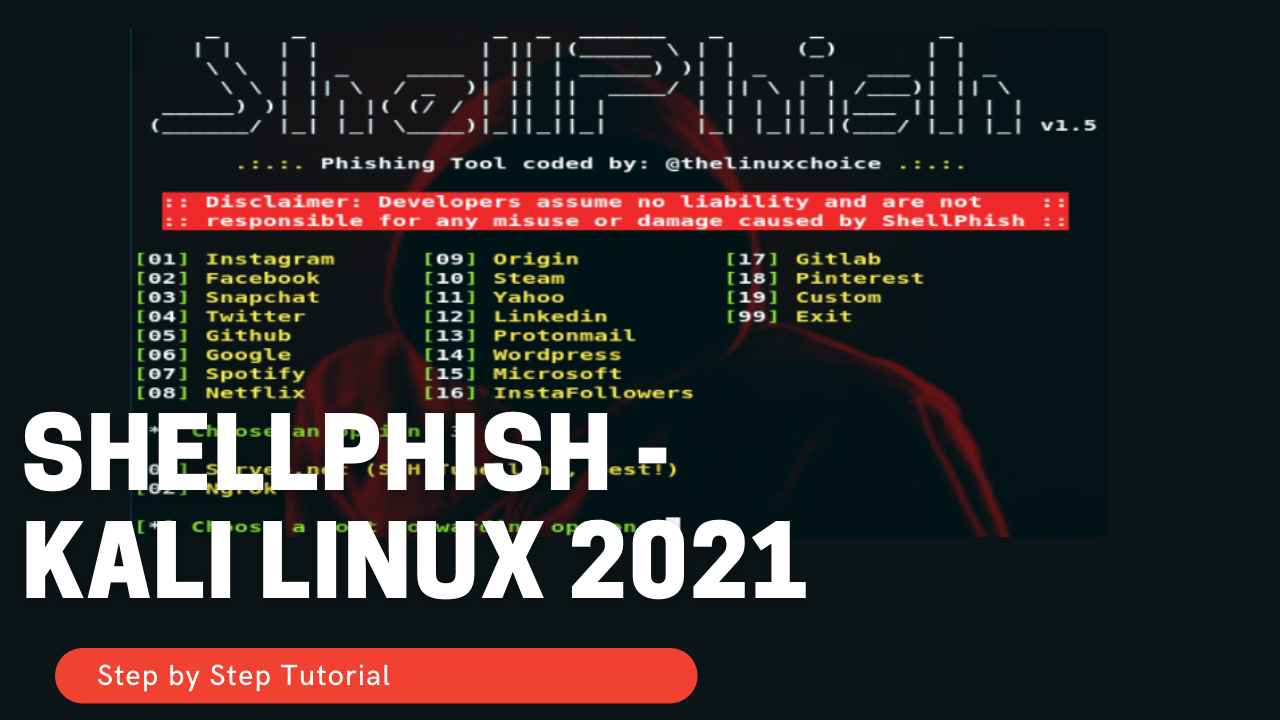
Hak5 WiFi Pineapple Mark VII – Captive Portal with Wireless Phishing & Nmap Scan
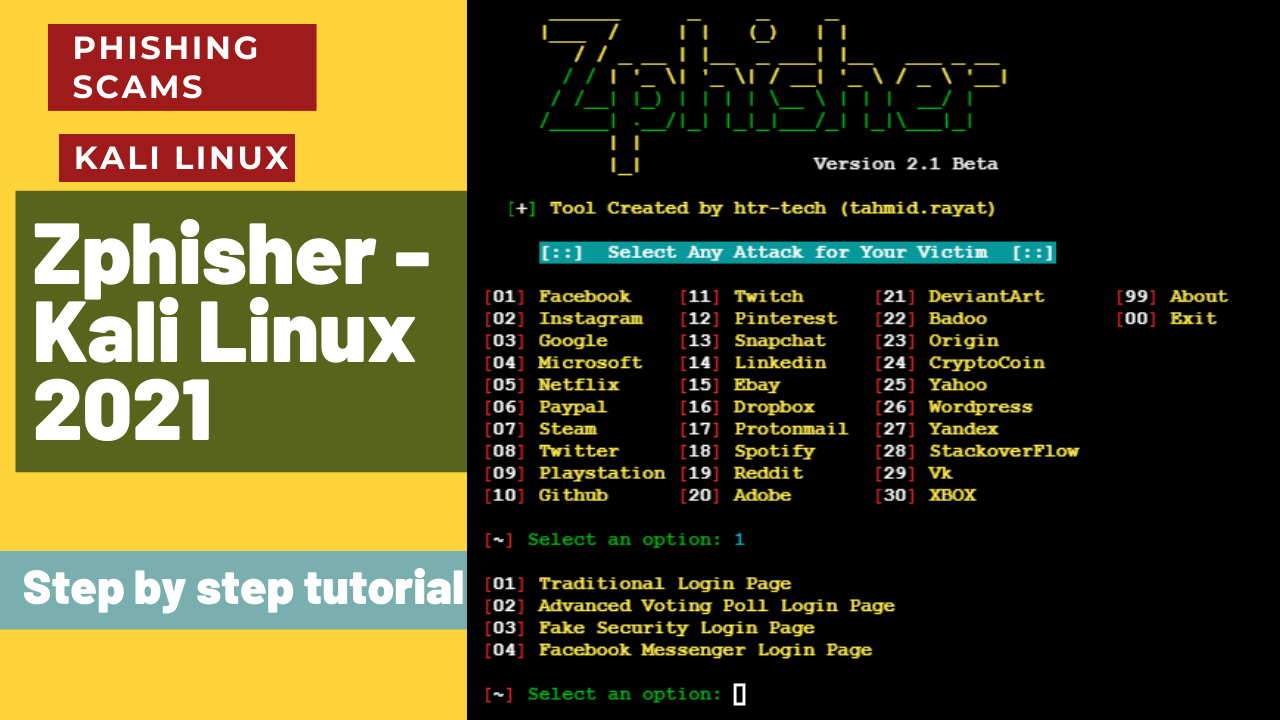
This tutorial demonstrates setting up Evil Portal on the WiFi Pineapple for phishing attacks. Learn how penetration testers can capture credentials on open Wi-Fi networks. Watch the video for step-by-step instructions.