In this video, I am going to demonstrate how you can use tools such as njRAT and JPS Virus Maker to set up trojans and viruses then demonstrate how you can deploy them.
If you are reading this blog post and do not have access to the CEH v11 tools, you can download njRAT from the link here
Malware – Trojans – Building our own Trojan with “njRAT”
In order to create our RAT, we’ll be using one of the most powerful RAT servers, njRAT. You can download it from the above link if you don’t have access to the CEH v11 tools. As soon as we execute the server’s .exe file in the folder, we’ll be redirected over to a pop-up window which will ask us for the default port.
Why build a RAT?
Attacker’s build their own Remote Access Trojans (RAT’s) in order to hack & control the victim’s system. So let’s create one and attack our target !!
How to get started?
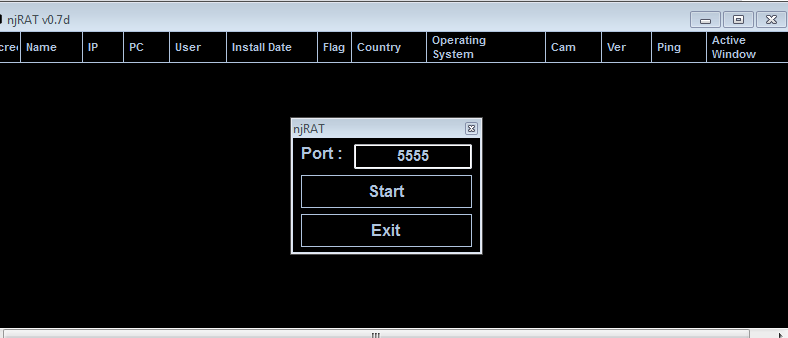
First, decide on a port number, we are going to use 5555 to start with, if you have a particular port you want to target, you can of course change this, click on start once you have set your port number.
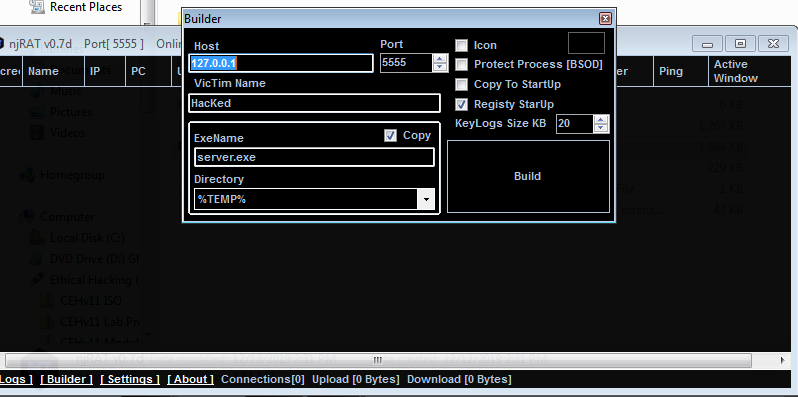
From the bottom menu (it’s quite hard to see!!), select build and it will then bring up the screen you can see below. Here you need to specify the attacker of your system machine i.e. 192.168.1.68, you can use a public or local IP here, this will create the bar door into our attacker machine. Now, give the victim target machine a name and specify the .exe file name, try to be creative if you are trying to fool them through a phishing scam. Once you are done select build and put it on your desktop. We now need to transfer the file to the victim machine.
How are we going to transfer our file to the victim machine?
The purpose of what we are doing is purely for ethical hacking, in a real life scenario, you would transfer the file through a phishing email. Today, we will used a HTTP tool to transfer the file onto our target computer.
On your attacker computer, download HFS onto your Windows VM using this link, once installed, drag and drop the trojan into HFS
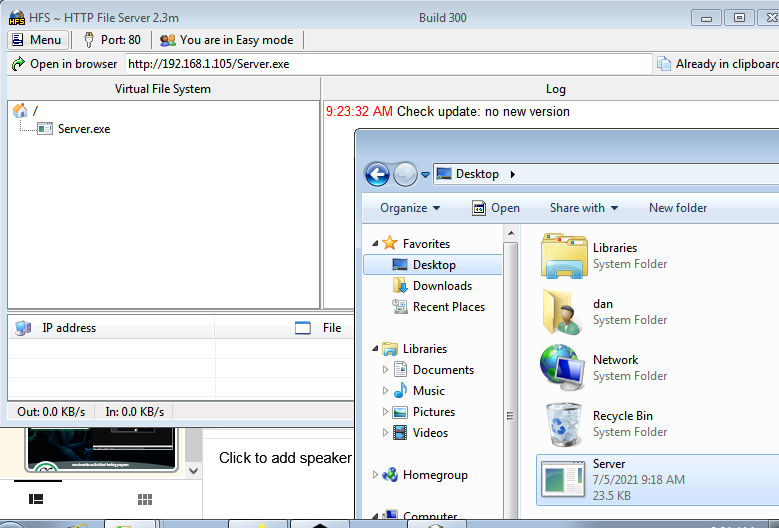
Go to the IP address of your attacker machine that you can see in NFS on the victim computer and download the file. You will need to make sure the firewall and antivirus are turned off for the purpose of this exercise.
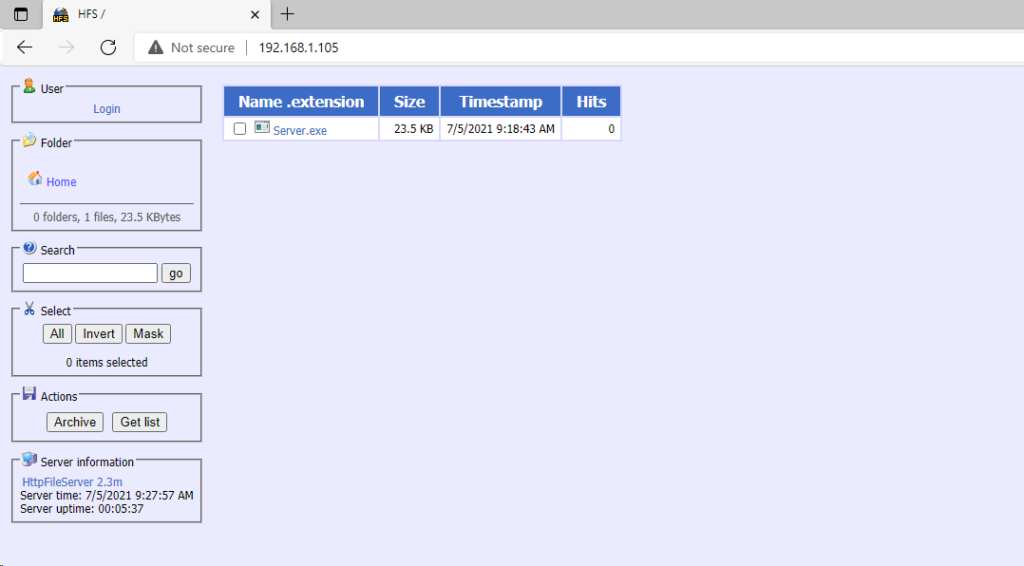
Windows may try to delete the file, select keep anyway (as per the below screenshoot), when you get to this screen, click on more info and select run anyway
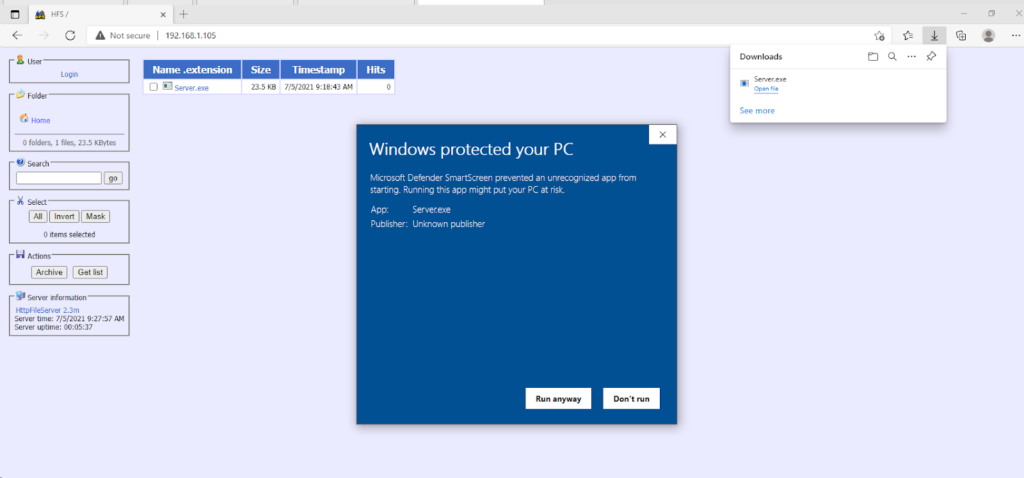
After running the file in the last step, go back to your attacker computer, if successful, you should see the screen below. If you have got this far, right click to see the different options that are available and refer to the course video at the top of this blog post.
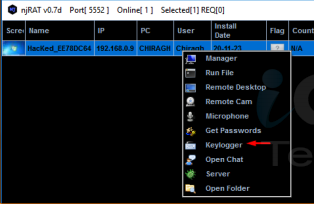
If you are looking to create a HTTP RAT or a virus using JPS virus maker, use the instructions from the video above or get in touch with us to find out more about our ethical hacking courses.