In this video, I am going to show you how to perform a wireless attack using Airgeddon. I will walk you through different wireless adapters that I use, how to install Alfa wireless adapter, how to install Airgeddon then lastly, how to perform an Evil Twin attack and mimic someones wifi.
Wireless Penetration Testing: Airgeddon
You’ll discover how to use airgeddon for Wi-Fi hacking in this article. It enables the capture of the WPA/WPA2 and PKMID handshakes in order to start a brute force assault on the Wi-Fi password key. It also aids in the creation of a fictitious AP for launching Evil Twin Attack by luring clients into the captive portal.
What will we cover in this article?
- Install Airgeddon & Usage
- Capturing Handshake & Deauthentication
- Aircrack Dictionary Attack for WPA Handshake
- Airacrack Brute Force Attack for WPA Handshake
- Hashcat Rule-Based Attack for WPA Handshake
- Evil Twin Attack
- PMKID Attack
Install Airgeddon & Usage
Airgrddon Features:
- Full support for 2.4Ghz and 5Ghz bands
- Assisted WPA/WPA2 personal networks Handshake file and PMKID capturing
- Interface mode switcher (Monitor-Managed)
- Offline password decrypting on WPA/WPA2 captured files for personal networks (Handshakes and PMKIDs) using a dictionary, bruteforce and rule-based attacks with aircrack, crunch and hashcat tools. Enterprise networks captured password decrypting based on john the ripper, crunch, asleap and hashcat tools.
- Evil Twin attacks (Rogue AP)
- WPS features
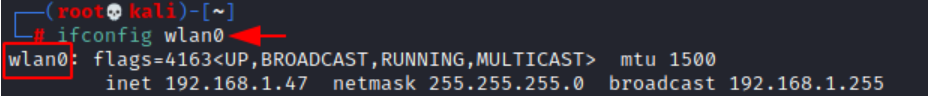
Download and run the airgeddon script by running the following commands in Kali Linux.
Note: execute the script as root or superuser.
git clone https://github.com/v1s1t0r1sh3r3/airgeddon.git
cd airgeddon
./airgeddon.sh
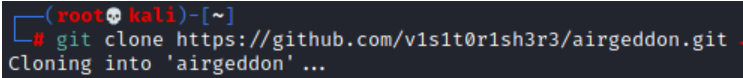
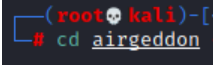
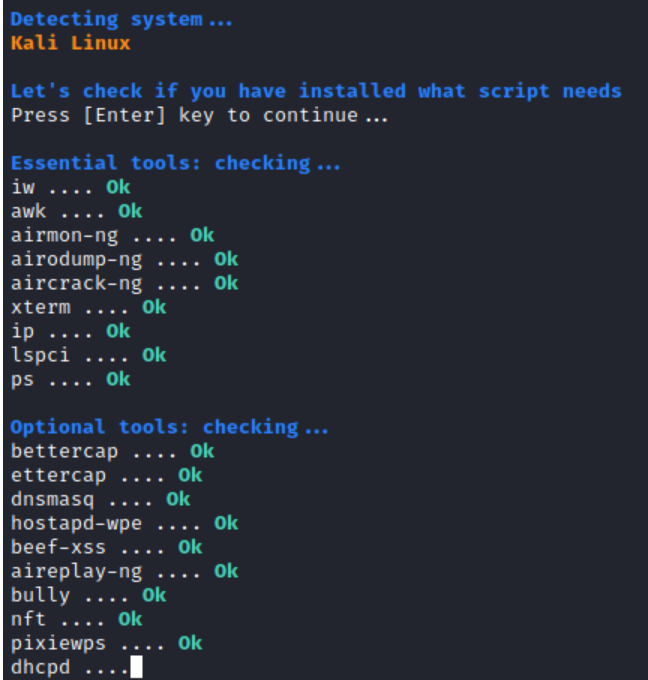
It will first check for all dependencies and necessary tools before launching this framework. It will attempt to instal the essential tools if they are missing, which may take some time. As indicated in the picture once the installation is complete, you will see the OK status for both required and optional tools.
Now you have got to this stage, the video at the top of this post will explore how to setup a PMKID and Evil Twin attack.