What should you be able to do by the end of this post?
This post is to provide readers with the basic concepts of sniffing packets using nmap and Wireshark on Kali Linux. The theory aspects to network scanning, ARP and TCP Half Open scans as well as how to establish a TCP Three-Way Handshake are discussed in this article, these skills are then demonstrated in the tutorial below.
Why would you want to sniff a packet and what would it allow a hacker to do?
Packet sniffing is the practice of gathering, collecting, and logging some or all packets that pass through a computer network, regardless of how the packet is addressed. A blackhat hacker may use this technique to:
- Read all your emails
- See all your passwords
- Know what websites you have visited
- See all the images from the websites you were on
- Capture account information (banks, credit cards) in detail
What is Network Scanning?
Network Scanning is the process of identifying Live Host (Ip Addresses) onto the network. The attacker uses this technique to discover his victim’s IP Address before carrying out an attack.
What tools can I use for Network Scanning?
For Kali – Netdiscover is an active/passive address reconnaissance tool, mainly developed for those wireless networks without dhcp server. It can also be used at hub/switch networks.
What are the different techniques used to identify and sniff packets using nmap and Wireshark?
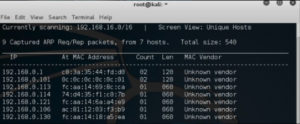
Arp Scan
An Arp–scan is a low-level network discovery tool used to associate physical (MAC) addresses to logical (IP) addresses. It’s used to identify network assets that may not normally be captured by network scanning devices. When assessing a system, we want to be able to identify vulnerabilities, the first thing we can do is recon Nmap allows us to identify different hosts on a network and different services the devices are running Arp scans will allow us to identify the state of a device and sniff packets from the host machine. This allows us to see who is the sender and who is the receiver
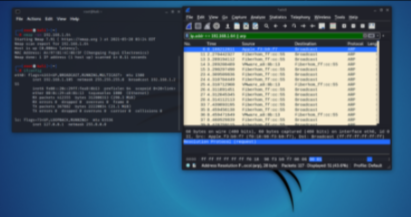
TCP Half Open
One of the more common and popular port scanning techniques is the TCP half-open port scan, sometimes referred to as an SYN scan. It’s a fast and sneaky scan that tries to find potential open ports on the target computer.
SYN packets request a response from a computer, and an ACK packet is a response. In a typical TCP transaction, there is an SYN, an ACK from the service, and a third ACK confirming message is received.
This scan is fast and hard to detect because it never completes the full TCP 3 way-handshake. The scanner sends an SYN message and just notes the SYN-ACK responses. The scanner doesn’t complete the connection by sending the final ACK: it leaves the target hanging.
Any SYN-ACK responses are possibly open ports. An RST(reset) response means the port is closed, but there is a live computer here. No responses indicate SYN is filtered on the network. An ICMP (or ping) no response also counts as a filtered response.
What does a TCP Half Open scan look like in Terminal and on Wireshark?
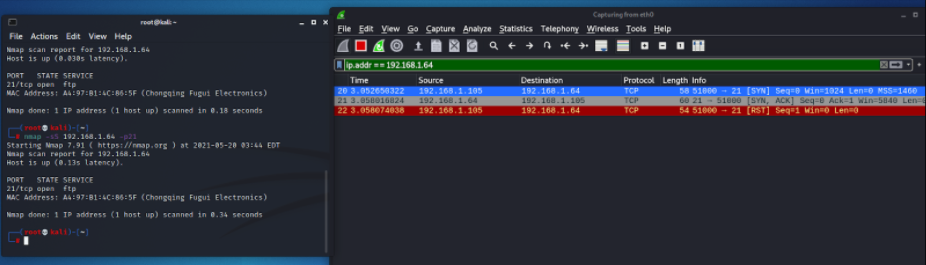
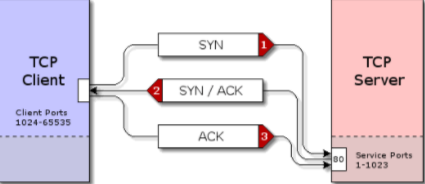
TCP Three-Way Handshake
THREE-WAY HANDSHAKE or a TCP 3-way handshake is a process that is used in a TCP/IP network to make a connection between the server and client. It is a three-step process that requires both the client and server to exchange synchronization and acknowledgment packets before the real data communication process starts.
The three-way handshake process is designed in such a way that both ends help you to initiate, negotiate, and separate TCP socket connections at the same time. It allows you to transfer multiple TCP socket connections in both directions at the same time.