This phishing tutorial for Ethical Hackers and Pen Testers explains phishing attacks and covers the phishing pages concept and why it is absolutely necessary to test an employee’s awareness after they have been through yearly phishing training. For this phishing tutorial, you will need Bit.ly, Kali Linux, Python3, SocialFish and an account with portmap.io to set up a VPN on Kali Linux.
Where to get started?
To start using SocialFish, we can check out the GitHub repository for information on previous versions and the mobile app that goes with the primary tool. Getting it running requires quite a few dependencies to be installed, so on a good internet connection, we can install everything with a few lines in a terminal window.
In a new terminal window, type the following commands to install the necessary dependencies, clone the repository, and run the set-up script.
$ git clone https://github.com/UndeadSec/SocialFish.git
$ sudo apt-get install python3 python3-pip python3-dev -y
$ cd SocialFish
$ python3 -m pip install -r requirements.txt
$ 𝚙𝚢𝚝𝚑𝚘𝚗𝟹 𝚂𝚘𝚌𝚒𝚊𝚕𝙵𝚒𝚜𝚑.𝚙𝚢 𝚞𝚜𝚎𝚛𝚗𝚊𝚖𝚎 𝚙𝚊𝚜𝚜𝚠𝚘𝚛𝚍
Once it is finished running, you should be ready to use SocialFish. We’ll be using our browser to interact with it, so open a FireFox window before proceeding to the next step.
Log in to the web interface
Now, let’s create a web interface that will help manage our phishing links. To do this, open a terminal window and type the following to change into the SocialFish folder. Pick a username and password to log in to the web interface, and substitute that for the “youruser” and “yourpassword” fields.
Select the target to clone
Inside the SocialFish portal, we can see some important information. At the top, we see the field for the website we want to clone, the website we want to redirect to, and the URL for our attack.
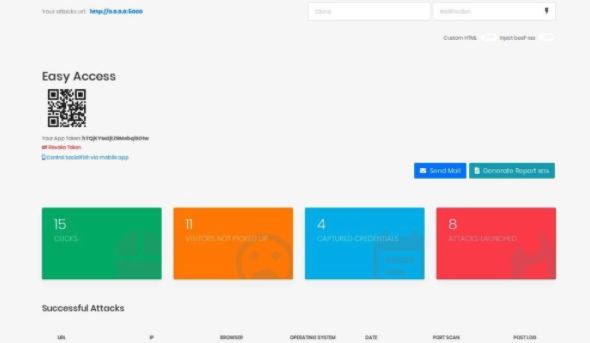
We can also see some information about links we’ve already created. In my case, I’ve already created eight attack links, which have attracted 15 clicks and four sets of captured credentials.
Links from video
https://linuxconfig.org/how-to-install-pip-on-kali-linuxhttps://github.com/UndeadSec/SocialFish
https://github.com/suljot/shellphish
https://github.com/An0nUD4Y/blackeye